Hackers Demand $70M After Kaseya Ransomware Attack
Hackers were on Monday demanding $70 million in bitcoin in exchange for data stolen during an attack on a US IT company that has shuttered hundreds of Swedish supermarkets.
Researchers believe more than 1,000 companies could have been affected by the attack on Miami-based firm Kaseya, which provides IT services to some 40,000 businesses around the world.
The FBI warned Sunday that the scale of the “ransomware” attack — a form of digital hostage-taking where hackers encrypt victims’ data and then demand money for restored access — is so large that it may be “unable to respond to each victim individually”.
Sweden’s Coop supermarket chain was among the most high-profile victims, with “a majority” of their 800 stores still closed three days after the hack paralysed its cash registers, spokesman Kevin Bell told AFP.
Coop is not a direct customer of Kaseya’s, but its IT subcontractor Visma Esscom was hit by the attack.
Bell stressed that the situation was looking “positive compared to a few days ago”, but the few hundred stores that have reopened were relying on alternative payment solutions, such as customers paying using their smartphones.
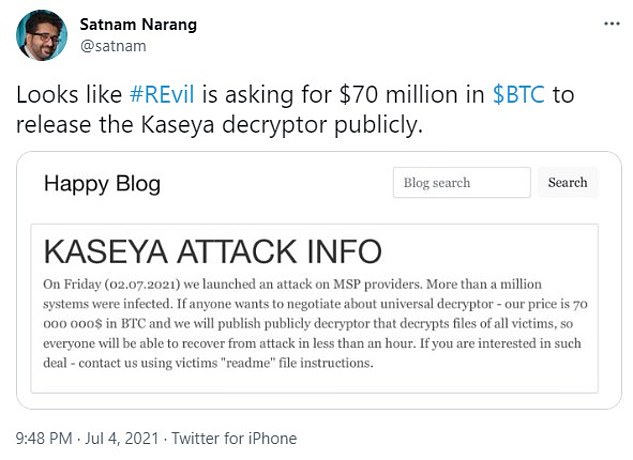
Experts believe the attack was probably carried out by REvil, a Russian-speaking hacking group known as a prolific perpetrator of ransomware attacks.
A post on Happy Blog, a site on the dark web previously associated with the group, claimed responsibility for the attack and said it had infected “more than a million systems”.
The FBI believes that REvil, which also goes by the name Sodinokibi, was behind a ransomware attack last month on global meat-processing giant JBS, which ended up paying $11 million in bitcoin to the hackers.
The blog post claiming responsibility for the Kaseya attack said the hackers would post a decryption tool online “so everyone will be able to recover from attack in less than an hour” — if they were handed $70 million in bitcoin.
Kaseya describes itself as a leading provider of IT and security management services to small and medium-sized businesses.
The company said Sunday that it believed the damage had been restricted to a “very small number” of customers using its signature VSA software, which lets companies manage networks of computers and printers from a single point.
But cybersecurity firm Huntress Labs said in a Reddit forum that it was working with partners targeted in the attack, and that the software was manipulated “to encrypt more than 1,000 companies”.
Kaseya said it had “immediately shut down” its servers after detecting the attack on Friday and warned its VSA customers to do the same, “to prevent them from being compromised.”
The company has released a tool allowing its customers to find out whether their own computer systems have been compromised by the attack.
– Russia-linked hackers strike again? –
In recent months numerous US companies, including the computer group SolarWinds and the Colonial oil pipeline, have been the victims of high-profile ransomware attacks blamed by the FBI on hackers based in Russian territory.
US President Joe Biden recently raised the threat in talks with Russian counterpart Vladimir Putin, and on Saturday he ordered a full investigation into the Kaseya attack.
While “the initial thinking was it was not the Russian government”, Biden said, “if it is either with the knowledge of and/or a consequence of Russia, then I told Putin we will respond.”
Loic Guezo, head of Clusif, a French association of cybersecurity experts, said the Kaseya attack bore a strong resemblance to last year’s spectacular attack against SolarWinds, a software company.
But he added that it was unclear why the hackers were this time demanding such a massive sum of money, and suggested it may have been done with political objectives to put pressure on the Biden administration.



